WHAT IS A SECURITY FRAMEWORK? A COMPREHENSIVE GUIDE
What is a Security Framework?
Are you looking to protect your business from cybercrime?
Are you concerned about the security of your business and data?
Have you heard of a security framework but don’t know what it is or how it can help protect your data?
In this comprehensive guide, we’ll provide a deep dive into what makes up a security framework and how it can help protect your business.
We’ll take an in-depth look at the fundamentals of a security framework, as well as the benefits that come with implementing one.
A security framework is an essential tool in reducing exposure and minimizing risks.
Security frameworks are a set of policies, standards, guidelines, and procedures used by organizations to protect their systems from unauthorized access or attack.
From choosing the right type of security framework for your organization to implementing it correctly, this blog post will provide guidance on how to develop and maintain a secure environment with the help of a security framework.
Learn about the types of security frameworks available as well as tips on monitoring and maintaining them so that you can take advantage of all their benefits!
What is a Security Framework?
A security framework is a set of policies, processes, and procedures that organizations use to protect their data and systems from cyber threats.
It tells organizations how to protect their digital assets, like networks, applications, devices, and data.
A security framework is a set of rules and guidelines that tells an organization’s information technology (IT) environment how much risk it can handle.
It serves as the foundation for developing effective cybersecurity strategies by providing clear objectives and expectations for protecting IT resources.
Benefits of a Security Framework
By making sure they have enough protection against bad actors, organizations can reduce their risk of cybercrime by putting in place a comprehensive security framework.
Additionally, it can provide visibility into potential risks so that appropriate countermeasures can be taken before any damage occurs.
Finally, having a well-defined security framework in place helps ensure compliance with applicable regulations or industry standards such as NIST Cybersecurity Framework or ISO 27001/27002.
A comprehensive security framework should include elements such as identity management, access control, encryption, patch management, incident response plans, vulnerability assessments, monitoring tools, user awareness training programs, disaster recovery plans, threat intelligence gathering capabilities, and network segmentation techniques, depending on the size and complexity of an organization’s IT infrastructure.
A security framework is a comprehensive approach to protecting an organization from cyber threats.
Types of Cyber Security Frameworks Best Practices
Security frameworks are an essential part of any organization’s cybersecurity program.
They give you a way to manage and protect sensitive data, systems, and networks from people who want to do harm.
The most commonly used security frameworks are the NIST Cybersecurity Framework (CSF), ISO 27001/27002, COBIT 5, CIS 18 Critical Security Controls, PCI DSS, GDPR, and HIPAA.
NIST Cybersecurity Framework (CSF)
The NIST Cybersecurity Framework (CSF) is a set of guidelines created by the National Institute of Standards and Technology (NIST) to help organizations better manage their cybersecurity risks.
This framework provides a common language that organizations can use to identify, assess, and manage their cybersecurity risks in a consistent manner.
The CSF is based on existing standards and practices, and provides a flexible and cost-effective approach to effectively manage cybersecurity risks. It is designed to be used by organizations of all sizes and can be tailored to the specific needs of an organization.
The CSF helps organizations better understand, manage, and improve their cybersecurity by giving them a set of core functions, profiles, and tiers that can be used to evaluate and prioritize risk management efforts.
The core functions of the CSF are Identify, Protect, Detect, Respond, and Recover.
These functions provide a common framework for organizations to use when developing and implementing their cybersecurity risk management program.
Within each of these core functions are categories of activities that are designed to help organizations better understand their current cybersecurity risks and identify areas for improvement.
The CSF’s profiles and tiers give organizations more information and guidance to help them prioritize their risk management activities.
The tiers provide a way to measure an organization’s cybersecurity posture and compare it to their peers.
The CSF also provides guidance on how to integrate cyber risk management into existing organizational processes and how to assess the effectiveness of an organization’s risk management program.
Overall, the NIST Cybersecurity Framework provides a comprehensive and unified approach to managing cybersecurity risks.
It helps organizations to better understand their risks, prioritize their risk management activities, and develop effective strategies to reduce their risks.
It is a useful tool for organizations of all sizes, and can be tailored to meet the specific needs of an organization.
ISO 27001 / ISO 27002
ISO 27001/27002 is an international standard created by the International Organization for Standardization (ISO).
It provides best practices on how to manage information security within an organization in order to protect it from cyber threats.
This standard includes topics such as access control policies & procedures; physical & environmental protection; personnel security; incident response planning; business continuity planning; system development & maintenance processes; cryptography controls; monitoring activities etc., all with the goal of ensuring secure operations across all aspects of the company’s IT infrastructure.
ISO 27001 is an international standard that outlines the requirements for an Information Security Management System (ISMS).
It provides a framework for organizations to manage their information security risks and protect their critical information assets.
ISO 27002 is a code of practice for information security management that provides guidelines and general principles for initiating, implementing, maintaining, and improving information security management within an organization.
It is based on the ISO 27001 standard, but provides additional guidance on how to meet the requirements of the standard.
Both ISO 27001 and ISO 27002 are important standards that organizations should consider when developing a security management system.
While ISO 27001 outlines the requirements for an ISMS, ISO 27002 provides more detailed guidance on how to meet those requirements.
COBIT 5
COBIT 5 is another widely used framework for governance and management of enterprise IT created by ISACA, which stands for Control Objectives for Information and Related Technologies .
It provides a comprehensive set of processes, organizational structures, best practices, and tools for IT governance and management.
COBIT 5 is based on a process model structure, which includes a set of 34 processes organized into four domains: Plan and Organize, Acquire and Implement, Deliver and Support, and Monitor and Evaluate.
COBIT 5 also includes a set of enabling factors, such as people, policies, and culture, that are necessary for successful IT governance and management.
COBIT 5 is meant to help organizations reach their IT governance and management goals by giving them advice on how to design, implement, and maintain an effective IT governance and management system.
COBIT 5 is designed to help organizations ensure that their IT investments are used effectively and efficiently.
It helps organizations reduce IT costs, improve IT performance, and align IT with business objectives. COBIT 5 also helps organizations improve IT security, reduce IT risks, and ensure compliance with government regulations.
COBIT 5 also helps organizations make better choices about how to invest in IT and make sure that IT assets are used in a responsible and ethical way.

CIS 18 Critical Security Controls
The Center for Internet Security came up with the CIS 18 Critical Security Controls, which are a list of the best practices for IT security.
They focus on stopping malware, phishing, and remote access, which are the most common ways to attack. The controls cover things like authentication, secure configurations, hardening the system, patch management, and responding to an incident.
The controls are organized into eighteen control objectives to help organizations prioritize their security efforts.
1. Inventory and Control of Enterprise Assets
2. Inventory and Control of Software Assets
3. Data Protection
4. Secure Configuration of Enterprise Assets and Software
5. Account Management
6. Access Control Management
7. Continuous Vulnerability Management
8. Audit Log Management
9. Email and Web Browser Protections
10. Malware Defenses
11. Data Recovery
12. Network Infrastructure Management
13. Network Monitoring and Defense
14. Security Awareness and Skills Training
15. Service Provider Management
16. Application Software Security
17. Incident Response Management
18. Penetration Testing
Payment Card Industry Data Security Standard PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organizations that handle cardholder data.
It was created to increase controls around cardholder data to reduce credit card fraud.
The standard is maintained by the Payment Card Industry Security Standards Council and applies to any organization that stores, processes, or transmits cardholder data.
The standard is designed to protect cardholder data from unauthorized access, disclosure, or use.
It is comprised of 12 requirements which include things such as: creating a secure network, protecting cardholder data, maintaining a vulnerability management program, and regularly testing security systems.
The standard applies to any organization, no matter how big or small, that processes, stores, or sends cardholder data.
All organizations that fall under the scope of the PCI DSS must implement the security measures outlined in the standard.
Failure to comply with the PCI DSS can lead to fines and/or other penalties imposed by the card brands or the acquiring bank.
GDPR
GDPR stands for “General Data Protection Regulation.” It is a set of rules that the European Union has put in place to make data protection for people in the EU stronger and more uniform.
It is designed to give individuals control over their personal data and ensure that businesses process it responsibly.
It gives individuals the right to access, rectify, and delete their data, as well as the right to object to the processing of their data.
It also sets out the legal requirements for organizations to protect the personal data that they hold.
GDPR applies to any organization, regardless of size or geography, that processes the personal data of EU citizens.
This means that if an organization processes the data of EU citizens, they must comply with GDPR, even if the organization is based outside of the EU.
In summary, GDPR gives individuals control over their personal data and ensures that businesses process it responsibly, setting out the legal requirements for organizations to protect the personal data that they hold.

HIPAA
HIPAA The Health Insurance Portability and Accountability Act (HIPAA) of 1996 is a federal law in the United States that protects the privacy of a person’s health information.
The law provides individuals with rights to access and control their health data, as well as set restrictions and conditions on the use and disclosure of the information by covered entities.
The law also requires covered entities to implement measures to protect the security and confidentiality of the information.
HIPAA was enacted to protect individuals and their healthcare providers from unnecessary intrusion, to reduce healthcare fraud and abuse, and to promote the efficient use of healthcare resources.
It applies to a wide range of entities, including hospitals, physicians, health insurers, and other healthcare providers.
HIPAA also sets out requirements for the use and disclosure of protected health information (PHI).
PHI includes any information that is created or received by a healthcare provider, health plan, or other healthcare related entity that can be used to identify an individual.
PHI must be used and disclosed in accordance with HIPAA regulations.
If PHI is used or shared without permission, it is against the law and can lead to civil and/or criminal penalties.
Key Takeaway: Security frameworks are essential for organizations to protect their data and systems from malicious actors.
The most common security frameworks are the NIST Cybersecurity Framework (CSF), ISO 27001/27002, COBIT 5, CIS 18 Critical Security Controls, PCI DSS, GDPR, and HIPAA.
All of these focus on reducing risks related to cyber threats while improving operational efficiency.
These frameworks provide guidance on topics such as asset management, access control policies & procedures, risk assessment, incident response planning, business continuity planning etc., in order to ensure secure operations across an organization’s IT infrastructure.
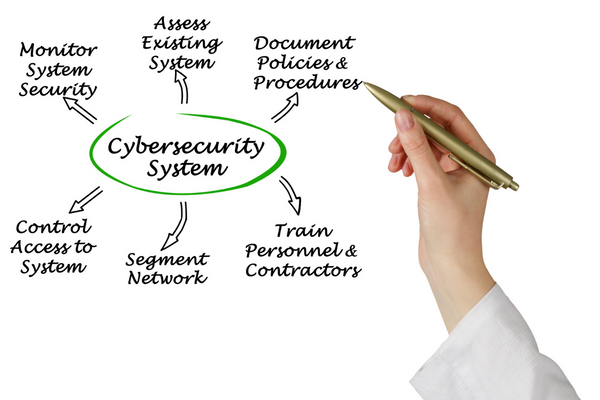
Implementing a Security Framework
Assessing the Current State of Your Organization’s Cybersecurity Program:
Before implementing a security framework, it is important to assess the current state of your organization’s cybersecurity program.
This includes evaluating existing policies and procedures, identifying any gaps in coverage or areas that need improvement, and understanding how cyber threats are impacting your organization.
Developing and Implementing Policies and Procedures for Your Organization’s Cybersecurity Program:
Once you have identified any weaknesses in your organization’s cybersecurity program, it is time to develop policies and procedures that will help protect against cyber threats.
These should include guidelines on user access control, data encryption methods, incident response plans, regular vulnerability scans, employee training programs, etc.
It is essential to ensure that all employees are trained on the best practices for protecting against cyber threats.
This can include topics such as password management techniques, recognizing phishing emails or malicious links/attachments sent via email or social media platforms like Facebook or Twitter.
Additionally, providing awareness campaigns about emerging trends in cybercrime can be beneficial too.
Having an effective security framework in place is essential to protecting your organization from cyber threats.
The next step is to understand the various tools and technologies available for strengthening your organization’s cybersecurity posture.
Monitoring and Maintaining Your Security Framework
Regularly reviewing your organization’s cybersecurity program, updating policies and procedures as needed, and conducting periodic audits to ensure compliance with regulations and best practices are all important steps in keeping your data secure.
Regularly Reviewing Your Organization’s Cybersecurity Program:
It is important to review the security framework on a regular basis in order to identify any potential vulnerabilities or weaknesses that may have been overlooked.
This can be done by conducting internal reviews of the system architecture, network configuration, user access controls, patch management processes, etc., as well as external assessments from third-party vendors or consultants.
Additionally, it is also important to stay up-to-date on industry trends and developments in order to ensure that the security framework remains relevant and effective.
Updating Policies and Procedures as Needed
As technology advances, so do cyber threats; therefore, it is necessary for organizations to regularly update their policies and procedures accordingly.
Organizations should assess their current policies against new threats or changes in technology in order to determine if additional measures need to be taken or existing ones updated/revised.
Additionally, organizations should also consider implementing new technologies such as encryption software or multi-factor authentication systems when appropriate.
Periodic audits are essential for ensuring that the security framework meets both regulatory requirements, such as GDPR, and industry best practices, such as NIST.
These audits should include technical assessments, like vulnerability scans, and procedural reviews, like employee training programs.
Organizations can use the results of these audits to refine their existing policies and procedures in order to maintain a robust cybersecurity posture going forward.
By regularly monitoring and maintaining your security framework, you can ensure that your organization’s cybersecurity program is up-to-date with the latest regulations and best practices.
Key Point: In order to stay ahead of cyber threats, it is important for organizations to regularly review and update their security framework.
This includes conducting internal reviews, external assessments, staying up-to-date on industry trends and developments, updating policies and procedures as needed, and performing periodic audits.
By doing so, organizations can ensure that their cybersecurity program remains relevant and effective while also meeting regulatory requirements.

Importance of Effective Security Framework
The importance of having an effective security framework in place cannot be overstated. A security framework is a set of policies, procedures, and guidelines that help organizations protect their systems from cyber threats.
It serves as the foundation for developing and implementing a comprehensive cybersecurity program that can effectively mitigate risk and protect data assets.
Having an effective security framework helps organizations stay compliant with industry regulations while also providing guidance on best practices to ensure the safety of their networks and data.
Security frameworks provide clear direction on how to develop secure systems, identify potential vulnerabilities, respond quickly to incidents, and recover from them quickly if needed.
They also help organizations prioritize which areas need more attention when it comes to protecting their digital assets.
Implementing a comprehensive cybersecurity program provides numerous benefits for businesses of all sizes.
It helps reduce risks associated with cyberattacks by ensuring all systems are up-to-date with the latest patches and updates; monitoring user activity; conducting regular vulnerability scans; training employees on proper cybersecurity protocols; enforcing strong password policies; encrypting sensitive data; using two-factor authentication where possible; regularly backing up important files offsite or in the cloud; utilizing firewalls or other protective measures as necessary; etc..
All these measures help create a secure environment where businesses can confidently store confidential information without fear of being compromised by malicious actors online.
Overall, having an effective security framework in place is essential for any organization looking to protect its digital assets from potential threats online today.
Implementing a comprehensive cybersecurity program will not only keep your business safe but also provide peace of mind knowing that your valuable information is protected against malicious attacks or intrusion attempts made by hackers or other criminals online.
To protect your business from cyber threats, you need to have a complete security framework in place.
Key Takeaway: A security framework is essential for any organization looking to protect its digital assets from cyber threats.
It provides clear direction on how to develop secure systems, identify potential vulnerabilities, respond quickly to incidents and recover quickly if needed.
Implementing a comprehensive cybersecurity program can help reduce risks associated with cyberattacks by enforcing strong password policies, encrypting sensitive data, using two-factor authentication and more.

FAQs in Relation to What is a Security Framework
What is meant by a security framework?
It provides an overall structure for how to approach cybersecurity and outlines the processes, tools, and techniques needed to effectively manage risk.
A security framework also helps organizations understand what they need to do in order to comply with industry regulations or standards such as ISO 27001 or NIST 800-53.
By following these frameworks, businesses can ensure their systems are secure while meeting compliance requirements.
What are the 3 key ingredients in a security framework?
1. Risk Assessment: A comprehensive risk assessment is essential to identify and prioritize security risks, vulnerabilities, and threats. This helps organizations develop a tailored security framework that addresses their specific needs.
2. Policies & Procedures: Establishing clear policies and procedures for the organization’s cybersecurity posture is key in ensuring compliance with industry standards and regulations. These should be regularly reviewed and updated as needed to keep up with changing technology or business objectives.
3. Security Controls: Implementing appropriate technical controls such as encryption, authentication, access control, firewalls etc., along with administrative controls like user training programs are important elements of any security framework to ensure data protection from malicious actors or accidental loss/damage due to human error.
What is the best security framework?
The best security framework for any organization depends on their individual needs and risk profile. However, the most widely accepted and comprehensive security frameworks are NIST 800-53, ISO 27001/27002, COBIT 5, and CIS 20 Critical Security Controls.
These frameworks provide organizations with a holistic approach to cyber security by covering topics such as asset management, access control systems, incident response plans, network monitoring tools and much more.
All of these frameworks have been proven effective in reducing an organization’s exposure to cybercrime while also providing guidance on how to maintain secure operations over time.
What is the security framework steps?
Cyb-Uranus’ security framework consists of five steps:
1. Identify – We assess the current cyber security posture and identify any existing vulnerabilities or gaps in protection.
2. Protect – We develop policies, procedures, and technical controls to protect data from unauthorized access or misuse.
3. Detect – We deploy monitoring systems to detect malicious activity as soon as possible after it occurs.
4. Respond – We create plans for responding quickly and effectively to incidents when they occur, including measures for containment, eradication, recovery, and reporting requirements.
5. Recover – Finally we help clients recover from an incident by providing guidance on restoring systems back to their pre-incident state while ensuring that all necessary precautions are taken against future attacks
Conclusion
In conclusion, a security framework is an essential part of any organization’s cyber security strategy. It provides the necessary guidance and structure to ensure that all areas of your business are adequately protected from cyber threats.
There are various types of security frameworks available, each with its own set of benefits and drawbacks.
When implementing a security framework, it is important to consider the specific needs and goals of your organization in order to select the most appropriate one for you.
Once implemented, it is also important to monitor and maintain your security framework on an ongoing basis in order to ensure that it remains effective against evolving threats.
By taking these steps, organizations can better protect themselves from potential cybercrime risks by having a secure “a security framework” in place.
Cyb-Uranus is the perfect partner to ensure your business is secure from cyber threats. Our team of experts will help you build a security framework that meets all industry standards and gives you peace of mind that your data, systems, and infrastructure are safe. We can provide tailored solutions for any size organization, so don’t wait another day—contact us now and let’s get started on building an effective security program!

